Palo Alto Networks® Next-generation Firewall Overview
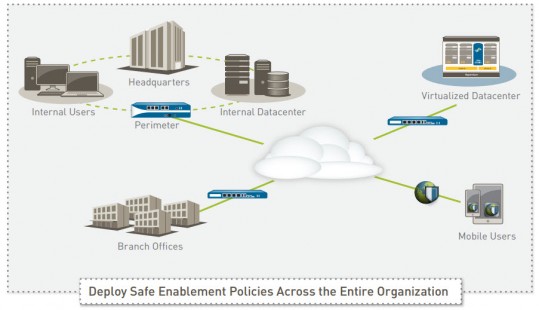
Fundamental shifts in application usage, user behavior, and network infrastructure create a threat landscape that exposes weaknesses in traditional port-based network security. Your users want access to an increasing number of applications operating across a wide range of device types often with little regard for the business or security risks. Meanwhile, datacenter expansion, network segmentation, virtualization, and mobility initiatives are forcing you to rethink how to enable access to applications and data, while protecting your network from a new, more sophisticated class of advanced threats that evade traditional security mechanisms.
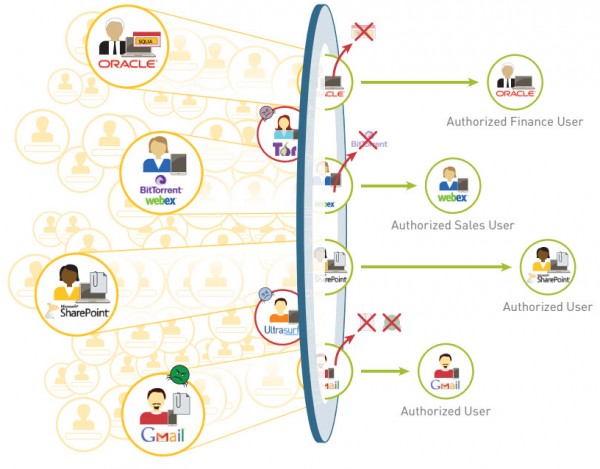
Historically, you were left with two basic choices—either block everything in the interest of network security, or enable everything in the interest of your business. These choices left little room for compromise. The Palo Alto Networks enterprise security platform provides you with a way to safely enable the applications your users need by allowing access while preventing cybersecurity threats.
Our next-generation firewall is the core of the enterprise security platform, designed from the ground up to address the most sophisticated threats. The next-generation firewall inspects all traffic—inclusive of applications, threats, and content—and ties it to the user, regardless of location or device type. The application, content, and user—the elements that run your business—become integral components of your enterprise security policy. The result is the ability to align security with your key business initiatives.