
FireEye, a leader in providing cyber security solutions, protects the most valuable assets in the world from those who have them in their sights. Our combination of technology, intelligence, and expertise — reinforced with the most aggressive incident response team — helps eliminate the impact of security breaches. We find and stop attackers at every stage of an incursion. With FireEye, you’ll detect cyber attacks as they happen, understand the risk they pose to your most valued assets, and have the resources to quickly respond and resolve security incidents. The FireEye Global Defense Community includes more than 2,500 customers across 65 countries, including over 150 of the Fortune 500.
FireEye Adaptive Defense
Technology. Intelligence. Expertise.
Cyber security is more than technology. As cyber attacks change, our defenses must evolve. Today’s security architecture must be agile, flexible, and deeply integrated. It must offer a far-reaching view of threats to prevent attacks and avert their worst effects.
Adaptive Defense Defined
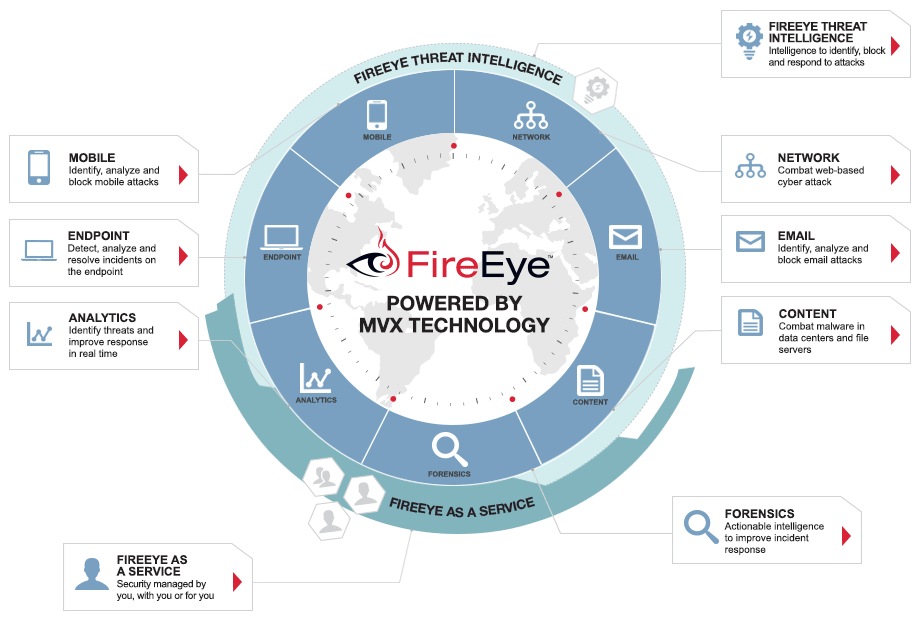
FireEye Adaptive Defense is a new approach to cyber security that delivers technology, expertise, and intelligence in a unified, nimble framework. You get the level of protection you want, delivered the way you want it.
- Our state-of-the-art technology protects you with our patented virtual-machine detection (MVX™) engine. Find cyber attacks that bypass signature-based tools and common sandboxes.
- Our security expertise comes from fighting the most skilled, persistent threat actors. Resolve data breaches quickly and prepare for future attacks.
- Our threat intelligence blends threat data from millions of virtual-machine detection engines around the world with the vast experience of our expert cyber security analysts. Hunt for new attacks, tools, and methods to keep your defenses up to date.
Adaptive Defense at Work
Most defenses focus on only one or two of these features. They miss most attacks. When they do detect a data breach, they can do little to fix it. Today’s architecture must continuously detect, prevent, analyze, and respond to threats.
FireEye Adaptive Defense:
- Detects cyber threats other security tools may be missing – in minutes, not months.
- Prevents many cyber attacks instantly and stops complex attacks before they cause lasting damage.
- Analyzes network traffic, files, and endpoint activity for a full view of your environment. Know what systems are affected and understand the impact.
- Responds quickly to attacks to reduce incident response times. Get the details and advice you need to remove the threat without disrupting operations.
Adaptive Defense Your Way
Adaptive Defense constantly evolves. It learns and improves to deal with new cyber threats. It conforms to your evolving needs. And it offers flexible purchase options to fit your accounting model.
Cover one threat vector or all of them with FireEye Threat Prevention Platforms– and scale as conditions change. Manage FireEye deployments yourself or partner with FireEye as a Service for outside expertise. And choose how much you want to know about attackers with three levels of FireEye Threat Intelligence.
Products
FireEye cyber security products combat today’s advanced persistent threats (APTs). As an integral piece of an Adaptive Defense strategy, our state-of-the-art network security offerings protect against cyber attacks that bypass traditional signature-based tools such as antivirus software, next-generation firewalls, and sandbox tools. View the FireEye Corporate Brochure to learn more about our offerings.
Network Security NX Series
Web security to detect and block malicious files,
communication channels, and exploit attempts
Advanced cyber attacks use the web as a primary threat vector to compromise key systems, perform reconnaissance on existing defenses, establish long-term control and access, and steal data.
FireEye Network Security (NX) products, now available in modular 2- and 4-Gbps appliances, enable organizations to prevent, detect, and respond to network-based zero day exploit attempts, web drive-by downloads, and advanced malware that routinely bypass conventional signature-reliant defenses.

Email Security EX Series and ETP
Detect and block spear phishing and
other email-based attacks
Cyber criminals often use email spear phishing attacks, as well as malicious file attachments and URLs in emails, to launch an advanced cyber attack. These email attacks routinely bypass conventional signature-based defenses such as antivirus and spam filters.
FireEye Email Security products (EX and ETP) protect against these cyber attacks. By detonating and analyzing suspicious email attachments and embedded URLs, and blocking anything malicious, organizations can prevent, detect, and respond to email-based cyber attacks. FireEye also provides anti-virus and anti-spam protection through Email Threat Prevention (ETP) in the cloud.

File Content Security FX Series
Detect and block malicious content hiding in file shares and SharePoint
Online file shares and portable file storage are vulnerable vectors used to launch advanced cyber attacks that can compromise key systems within an organization.
File content security (FX Series) products helps prevent, detect, and respond to cyber attacks by scanning internal file shares for malicious content brought into an organization from outside sources, such as online file shares and portable file storage devices.

Endpoint Security HX Series
Detect and respond to targeted cyber attacks and zero-day exploits on the endpoint
Adaptive security requires monitoring of all threat vectors including fast, accurate assessments of potential cyber attacks tracked to endpoint activity.
The HX series of endpoint security products provides organizations with the ability to continuously monitor endpoints for advanced malware and indicators of compromise that routinely bypass signature-based and defense-in-depth security systems.
Endpoint Forensics Mandiant Intelligent Response (MIR)
Remotely detect and investigate cyber attacks on endpoints across the enterprise
The ability to perform fast, targeted investigations across thousands of endpoints is critical when trying to prevent cyber attacks.
The Endpoint Forensics product (also known as Mandiant Intelligent Response or MIR) is an endpoint security tool that helps organizations monitor for indicators of compromise on endpoints and respond to cyber attacks on the endpoint before critical data loss occurs.
Mobile Security Mobile Threat Prevention
Detect and prevent spying, profiling and cyber attacks leveraging mobile devices
Malicious mobile apps leverage private information, such as contact lists and calendar details, and mobile features, such as cameras and microphones, to spy, profile, or conduct cyber attacks.
FireEye Mobile Security (Mobile Threat Prevention) detects and prevents these mobile threats and provides visibility into mobile device security trends across the enterprise. FireEye Mobile Threat Prevention also integrates with industry leading mobile device management (MDM) providers.

Enterprise Forensics PX and IA series
Network forensics and investigation analysis at enterprise scale
As recent cyber security breach headlines reveal, the key to minimizing the impact of a security incident is early detection and swift investigation, which requires powerful forensics capabilities. When attacked, an enterprise needs to be able to rapidly investigate and determine the scope and impact of the incident so they can effectively contain the threat and re-secure their network.
The FireEye Network Forensics Platform (PX series) and the Investigation Analysis system (IA series) are a powerful combination, pairing the industry’s fastest, lossless network data capture and retrieval solution with centralized analysis and visualization. High performance packet capture with analysis tools to aid investigation efforts complement other FireEye threat prevention and detection capabilities.
Malware Analysis AX Series
Safely execute and inspect malware in a secure environment
An important part of preventing and detecting future cyber attacks is analyzing current ones. Using malware analysis tools, cyber security experts can analyze the attack lifecycle and glean important forensic details to enhance their threat intelligence.
Malware Analysis (AX series) products provide a secure environment to test, replay, characterize, and document advanced malicious activities. Malware Analysis shows the cyber attack lifecycle, from the initial exploit and malware execution path to callback destinations and follow-on binary download attempts.

Threat Analytics Platform Security Data Analytics
Detect and respond to threats discovered through event and data stream analysis
Information technology systems and applications produce a continuous stream of event and log details that can reveal suspicious behavior. The challenge is proactively filtering through the noise to identify real threats.
The Threat Analytics Platform (TAP) applies threat intelligence, expert rules, and advanced security data analytics to noisy event data streams. By revealing suspicious behavior patterns and generating alerts that matter, security teams can prioritize and optimize their response efforts.

